Biotech Cybersecurity Report 2025: Inside the Exposure of DNA and Health Records
- Sekurno

- Jul 31, 2025
- 3 min read
Updated: Aug 7, 2025
In Under Two Hours…
We uncovered exposed genomic data and over 300,000 patient records —No exploits. No brute force. Just misconfigured environments, unauthenticated endpoints, and publicly accessible data.
The first case wasn’t a one-off. It revealed a deeper pattern:
Systemic cybersecurity failures across biotech platforms — even those handling genomic sequences, diagnostics, and sensitive health data.
So we widened the lens.
Why Biotech ≠ Normal SaaS
Biotech companies aren’t just storing user profiles and billing info. They’re managing:

These aren’t just marketing analytics, they’re identity, prognosis, and privacy — and the stakes are much higher.
Our Methodology
We did what attackers do — legally.
OSINT & metadata analysis
Public code + subdomain mapping
Open API inspection
No brute-force, no auth bypass, no active probing
Every finding was made using passive techniques in publicly available environments.
What We Found
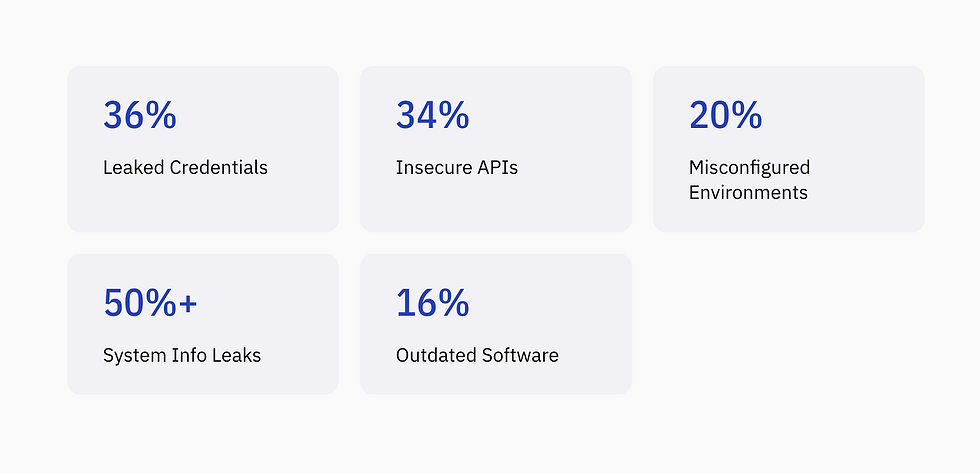
In our review of 50 public-facing biotech companies, we uncovered 64 security issues — many of which were publicly accessible with no login, scanning tools, or exploits required.
The most common exposures included:
Genomic reports accessible via direct URLs
Unauthenticated APIs leaking personal and patient data
Secrets and private keys embedded in front-end code
Exposed admin dashboards and staging environments
Outdated infrastructure with known vulnerabilities
These weren’t isolated. They showed up across early-stage startups and well-funded biotech platforms alike — including companies with millions in revenue and active user bases.
The graphic above highlights the top 5 recurring vulnerability patterns we found — reflecting just how widespread basic security hygiene failures remain in the biotech ecosystem.
Risk Severity Breakdown
We categorized all 64 issues by severity. Here’s what we found:
Even platforms with no “Critical” issues had overlapping weaknesses, creating a compound risk.
“We didn’t spend more than two hours per company, and yet we identified exposed DNA data, multiple misconfigurations, weak (or even absent) authentication, exposed client databases, and more.We find this extremely concerning, as trust is fundamental to the evolution of this industry—and our findings show that this trust can be easily undermined.”— Demyd Maiornykov, CEO, Sekurno
Why This Puts Biotech at Risk
These aren’t just technical flaws — they’re growth-blocking risks. Unchecked vulnerabilities like exposed APIs or misconfigured infrastructure can trigger consequences that ripple through your entire business:
Sensitive health data leaks (PHI/PII) can erode user trust overnight.
Unauthenticated APIs open doors to unauthorized access and data scraping.
Compliance violations with HIPAA, GDPR, and ISO standards can lead to audits, penalties, and failed renewals.
Partnerships and M&A deals often stall when security gaps appear during due diligence.
And worst of all, your reputation as a trustworthy biotech company can vanish with a single breach.
Security isn’t just a technical checkbox. In biotech, it’s a business imperative.
What You Can Do Now
Here are five immediate steps biotech companies can take to reduce exposure and build long-term resilience:
Harden your APIs — Enforce strong authentication, validate input, and apply rate limiting.
Lock down non-production environments — Staging and dev should never be publicly accessible.
Monitor for leaked credentials and secrets — Check public repos, packages, and logs continuously.
Map your public attack surface — Know what’s exposed externally, from domains to metadata.
Bake security into your SDLC — Embed checks early, not just before audits.
Security maturity isn’t about perfection. It’s about visibility, accountability, and continuous hardening.
Get the Full Report
Want to dive deeper? The Biotech Cybersecurity Report 2025 covers:
The top 5 most common and critical vulnerability types
Real-world examples of what attackers could access — passively
Strategic lessons from the 23andMe breach
Clear, actionable guidance for engineering, compliance, and leadership teams